LiME is a Loadable Kernel Module (LKM), which allows the acquisition of volatile memory from Linux and Linux-based devices, allows full memory captures .
Download from Github : https://github.com/504ensicsLabs/LiME
Looks like below :-
Go to the directory Src / then type the command Make
Once the donce the make command kernel object file will
create with the extension.ko
Use below command to extract the memory dump file.
# Sudo
insmod ./keranlobjectname.ko ‘’path = /root/Desktop/dump_filename.mem format=raw”
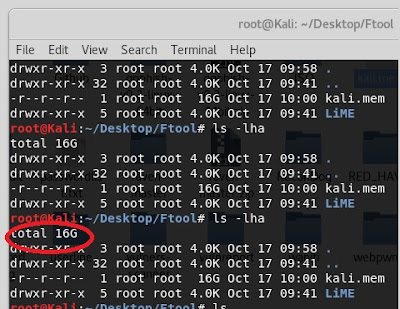
Open another terminal and
check the size – ls –lha
Use Volatility to do the analysis .
Volatility Framework - Volatile memory extraction utility framework
============================================================================ The Volatility Framework is a completely open collection of tools, implemented in Python under the GNU General Public License, for the extraction of digital artifacts from volatile memory (RAM) samples.