Saturday, October 9, 2021
MITRE ATT&CK TTPs - SIMULATION
ATOMIC RED TREAM >> AUTOMATE SIMULATION
Simulate mimicking MITRE ATT&CKS using ART and Custom developed scripts
This will reveal the maturity of SOC/SIEM detection capability when its come to a real adversarial attacks.
Here we are ging to add 400+ test cases -One by One
Work in progress ! Post soon !!!!!
Wednesday, December 13, 2017
V3n0M - Web Vulnerability Scan Tool
Vulnerability Scanner for SQLi/XSS/LFI/RFI
V3n0M is a free and open source scanner. Evolved from baltazar's scanner, it has adapted several new features that improve fuctionality and usability. It is mostly experimental software.
This program is for finding and executing various vulnerabilities.
https://github.com/v3n0m-Scanner/V3n0M-Scanner
Install note
Clone the repository:
$ git clone https://github.com/v3n0m-Scanner/V3n0M-Scanner.git
Then go inside:
$ cd V3n0M-Scanner/
Then install it:
$ python3 setup.py install --user
Note for Ubuntu : Please make sure you have installed -->
sudo apt-get install python3-bs4 and apt-get install python3-setuptools
For Kali : Please make sure installed -->
apt-get install python3-dev apt-get install python-dev
Tuesday, October 17, 2017
Memory Forensics - Lime | Volatility
LiME is a Loadable Kernel Module (LKM), which allows the acquisition of volatile memory from Linux and Linux-based devices, allows full memory captures .
Download from Github : https://github.com/504ensicsLabs/LiME
Looks like below :-
Go to the directory Src / then type the command Make
Once the donce the make command kernel object file will
create with the extension.ko
Use below command to extract the memory dump file.
# Sudo
insmod ./keranlobjectname.ko ‘’path = /root/Desktop/dump_filename.mem format=raw”
Open another terminal and
check the size – ls –lha
Use Volatility to do the analysis .
Volatility Framework - Volatile memory extraction utility framework
============================================================================ The Volatility Framework is a completely open collection of tools, implemented in Python under the GNU General Public License, for the extraction of digital artifacts from volatile memory (RAM) samples.
Monday, October 9, 2017
Secure Sockets Layer (SSL) and Transport Layer Security (TLS) Concepts | Encryption Methods | Digital Certificates
Secure Sockets Layer (SSL) and Transport Layer Security (TLS) concepts
The SSL and TLS protocols enable two parties to identify and authenticate each other and communicate with confidentiality and data integrity.
The SSL and TLS protocols provide communications security over the internet, and allow client/server applications to communicate in a way that is confidential and reliable. The protocols have two layers: a Record Protocol and a Handshake Protocol, and these are layered above a transport protocol such as TCP/IP. They both use asymmetric and symmetric cryptography techniques.
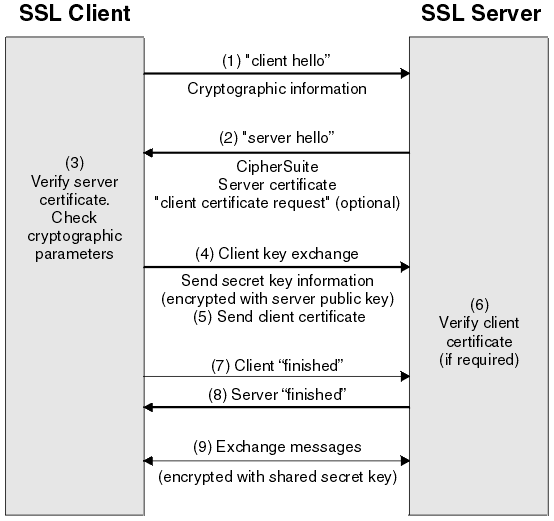
An SSL or TLS connection is initiated by an application, which becomes the SSL or TLS client. The application which receives the connection becomes the SSL or TLS server. Every new session begins with a handshake, as defined by the SSL or TLS protocols.
overview of the SSL or TLS handshake

Symmetric vs. Asymmetric Encryption

The simplest kind of encryption that involves only one secret key to cipher and decipher information. Symmetrical encryption is an old and best-known technique. It uses a secret key that can either be a number, a word or a string of random letters. It is a blended with the plain text of a message to change the content in a particular way. The sender and the recipient should know the secret key that is used to encrypt and decrypt all the messages. Blowfish, AES, RC4, DES, RC5, and RC6 are examples of symmetric encryption. The most widely used symmetric algorithm is AES-128, AES-192, and AES-256.
The main disadvantage of the symmetric key encryption is that all parties involved have to exchange the key used to encrypt the data before they can decrypt it.
Asymmetrical Encryption

Asymmetrical encryption is also known as public key cryptography, which is a relatively new method, compared to symmetric encryption. Asymmetric encryption uses two keys to encrypt a plain text. Secret keys are exchanged over the Internet or a large network. It ensures that malicious persons do not misuse the keys. It is important to note that anyone with a secret key can decrypt the message and this is why asymmetrical encryption uses two related keys to boosting security. A public key is made freely available to anyone who might want to send you a message. The second private key is kept a secret so that you can only know.
A message that is encrypted using a public key can only be decrypted using a private key, while also, a message encrypted using a private key can be decrypted using a public key. Security of the public key is not required because it is publicly available and can be passed over the internet. Asymmetric key has a far better power in ensuring the security of information transmitted during communication.
Asymmetric encryption is mostly used in day-to-day communication channels, especially over the Internet. Popular asymmetric key encryption algorithm includes EIGamal, RSA, DSA, Elliptic curve techniques, PKCS.
Asymmetric Encryption in Digital Certificates
To use asymmetric encryption, there must be a way of discovering public keys. One typical technique is using digital certificates in a client-server model of communication. A certificate is a package of information that identifies a user and a server. It contains information such as an organization’s name, the organization that issued the certificate, the users’ email address and country, and users public key.
When a server and a client require a secure encrypted communication, they send a query over the network to the other party, which sends back a copy of the certificate. The other party’s public key can be extracted from the certificate. A certificate can also be used to uniquely identify the holder.
SSL/TLS uses both asymmetric and symmetric encryption, quickly look at digitally signed certificates issued by trusted certificate authorities (CAs).
Digital certificates
Digital certificates protect against impersonation, certifying that a public key belongs to a specified entity. They are issued by a Certificate Authority.
Digital certificates provide protection against impersonation, because a digital certificate binds a public key to its owner, whether that owner is an individual, a queue manager, or some other entity. Digital certificates are also known as public key certificates, because they give you assurances about the ownership of a public key when you use an asymmetric key scheme. A digital certificate contains the public key for an entity and is a statement that the public key belongs to that entity:
- When the certificate is for an individual entity, the certificate is called a personal certificate or user certificate.
- When the certificate is for a Certificate Authority, the certificate is called a CA certificate or signer certificate.
Thursday, July 20, 2017
Sunday, July 16, 2017
XssPy - Cross Site Scripting Scanner
XssPy - Web Application XSS Scanner
XssPy is a python tool for finding Cross Site Scripting vulnerabilities in websites. This tool is the first of its kind. Instead of just checking one page as most of the tools do, this tool traverses the website and find all the links and subdomains first. After that, it starts scanning each and every input on each and every page that it found while its traversal. It uses small yet effective payloads to search for XSS vulnerabilities.
The tool has been tested parallel with paid Vulnerability Scanners and most of the scanners failed to detect the vulnerabilities that the tool was able to find. Moreover, most paid tools scan only one site whereas XSSPY first finds a lot of subdomains and then scan all the links altogether.
The tool comes with:
- Short Scanning
- Comprehensive Scanning
- Finding subdomains
- Checking every input on every page
~ How to Use:
Installation:
Type the following in the terminal.
git clone https://github.com/faizann24/XssPy/ /opt/xsspy
The tool works on Python 2.7 and you should have mechanize installed. If mechanize is not installed, type "pip install mechanize" in the terminal.
https://github.com/faizann24/XssPy
Tuesday, June 13, 2017
Arachni - Web Application Security Scanner Framework
Arachni is a feature-full, modular, high-performance Ruby framework aimed towards helping penetration testers and administrators evaluate the security of web applications.
It is smart, it trains itself by monitoring and learning from the web application's behavior during the scan process and is able to perform meta-analysis using a number of factors in order to correctly assess the trustworthiness of results and intelligently identify (or avoid) false-positives.
Unlike other scanners, it takes into account the dynamic nature of web applications, can detect changes caused while travelling through the paths of a web application’s cyclomatic complexity and is able to adjust itself accordingly. This way, attack/input vectors that would otherwise be undetectable by non-humans can be handled seamlessly.
Moreover, due to its integrated browser environment, it can also audit and inspect client-side code, as well as support highly complicated web applications which make heavy use of technologies such as JavaScript, HTML5, DOM manipulation and AJAX.
Finally, it is versatile enough to cover a great deal of use cases, ranging from a simple command line scanner utility, to a global high performance grid of scanners, to a Ruby library allowing for scripted audits, to a multi-user multi-scan web collaboration platform.
Note: Despite the fact that Arachni is mostly targeted towards web application security, it can easily be used for general purpose scraping, data-mining, etc. with the addition of custom components.
A stable, efficient, high-performance framework
Check, report and plugin developers are allowed to easily and quickly create and deploy their components with the minimum amount of restrictions imposed upon them, while provided with the necessary infrastructure to accomplish their goals.
Furthermore, they are encouraged to take full advantage of the Ruby language under a unified framework that will increase their productivity without stifling them or complicating their tasks.
Moreover, that same framework can be utilized as any other Ruby library and lead to the development of brand new scanners or help you create highly customized scan/audit scenarios and/or scripted scans.
Simplicity
Although some parts of the Framework are fairly complex you will never have to deal them directly. From a user’s or a component developer’s point of view everything appears simple and straight-forward all the while providing power, performance and flexibility.
From the simple command-line utility scanner to the intuitive and user-friendly Web interface and collaboration platform, Arachni follows the principle of least surprise and provides you with plenty of feedback and guidance.
In simple terms
Arachni is designed to automatically detect security issues in web applications. All it expects is the URL of the target website and after a while it will present you with its findings.
Features
General
- Cookie-jar/cookie-string support.
- Custom header support.
- SSL support with fine-grained options.
- User Agent spoofing.
- Proxy support for SOCKS4, SOCKS4A, SOCKS5, HTTP/1.1 and HTTP/1.0.
- Proxy authentication.
- Site authentication (SSL-based, form-based, Cookie-Jar, Basic-Digest, NTLMv1, Kerberos and others).
- Automatic log-out detection and re-login during the scan (when the initial login was performed via the
autologin,login_scriptorproxyplugins). - Custom 404 page detection.
- UI abstraction:
- Command-line Interface.
- Web User Interface.
- Pause/resume functionality.
- Hibernation support -- Suspend to and restore from disk.
- High performance asynchronous HTTP requests.
- With adjustable concurrency.
- With the ability to auto-detect server health and adjust its concurrency automatically.
- Support for custom default input values, using pairs of patterns (to be matched against input names) and values to be used to fill in matching inputs.
Integrated browser environment
Arachni includes an integrated, real browser environment in order to provide sufficient coverage to modern web applications which make use of technologies such as HTML5, JavaScript, DOM manipulation, AJAX, etc.
In addition to the monitoring of the vanilla DOM and JavaScript environments, Arachni's browsers also hook into popular frameworks to make the logged data easier to digest:
- JQuery
- AngularJS
In essence, this turns Arachni into a DOM and JavaScript debugger, allowing it to monitor DOM events and JavaScript data and execution flows. As a result, not only can the system trigger and identify DOM-based issues, but it will accompany them with a great deal of information regarding the state of the page at the time.
Full Detail
||||||https://github.com/Arachni/arachni
KALI LINUX: Download and Extract Arachni
extract :----- tar -xvzf arachni-1.5.1-0.5.12-linux-x86_64.tar.gz
:~terminal : ./arachni_web
:~terminal : ./arachni_rpcd
This start's arachni web scanner & can access at: localhost:9292
User Name: admin@admin.admin
Password: administrator
KALI LINUX: Download and Extract Arachni
extract :----- tar -xvzf arachni-1.5.1-0.5.12-linux-x86_64.tar.gz
:~terminal : ./arachni_web
:~terminal : ./arachni_rpcd
This start's arachni web scanner & can access at: localhost:9292
User Name: admin@admin.admin
Password: administrator
ZAP (OWASP : ZAP)
OWASP : ZAP
Zed Attack Proxy (ZAP) is one of the world’s most popular free security tools . It can help you automatically find security vulnerabilities in your web applications while you are developing and testing your applications. Its also a great tool for experienced pentesters to use for manual security testing.
These are the key functionalities of ZAP:
- Intercepting Proxy
- Automatic Scanner
- Traditional but powerful spiders
- Fuzzer
- Web Socket Support
- Plug-n-hack support
- Authentication support
- REST based API
- Dynamic SSL certificates
- Smartcard and Client Digital Certificates support
You can either use this tool as a scanner by inputting the URL to perform scanning, or you can use this tool as an intercepting proxy to manually perform tests on specific pages.
|||||Download ZAP : https://github.com/zaproxy/zaproxy
WAPITI - Web Application Security Auditor
WAPITI - VERSION 2.3.0 Wapiti is a web application security auditor. Requirements ============ In order to work correctly, Wapiti needs : + Python 2.x where x is >= 6 (2.6, 2.7...) + python-requests v1.2.3 or more ( http://docs.python-requests.org/en/latest/ ) + BeautifulSoup ( http://www.crummy.com/software/BeautifulSoup/ ) + python-xml How it works ============ Wapiti works as a "black-box" vulnerability scanner, that means it won't study the source code of web applications but will work like a fuzzer, scanning the pages of the deployed web application, extracting links and forms and attacking the scripts, sending payloads and looking for error messages, special strings or abnormal behaviors. General features ================ + Generates vulnerability reports in various formats (HTML, XML, JSON, TXT...) + Can suspend and resume a scan or an attack + Can give you colors in the terminal to highlight vulnerabilities + Different levels of verbosity + Fast and easy way to activate/deactivate attack modules + Adding a payload can be as easy as adding a line to a text file Browsing features ================= + Support HTTP and HTTPS proxies + Authentication via several methods : Basic, Digest, Kerberos or NTLM + Ability to restrain the scope of the scan (domain, folder, webpage) + Automatic removal of a parameter in URLs + Safeguards against scan endless-loops (max number of values for a parameter) + Possibility to set the first URLs to explore (even if not in scope) + Can exclude some URLs of the scan and attacks (eg: logout URL) + Import of cookies (get them with the wapiti-cookie and wapiti-getcookie tools) + Can activate / deactivate SSL certificates verification + Extract URLs from Flash SWF files + Try to extract URLs from javascript (very basic JS interpreter) + HTML5 aware (understand recent HTML tags) Supported attacks ================= + Database Injection (PHP/ASP/JSP SQL Injections and XPath Injections) + Cross Site Scripting (XSS) reflected and permanent + File disclosure detection (local and remote include, require, fopen, readfile...) + Command Execution detection (eval(), system(), passtru()...) + XXE (Xml eXternal Entity) injection + CRLF Injection + Search for potentially dangerous files on the server (thanks to the Nikto db) + Bypass of weak htaccess configurations + Search for copies (backup) of scripts on the server Wapiti supports both GET and POST HTTP methods for attacks. It also supports multipart and can inject payloads in filenames (upload). Display a warning when an anomaly is found (for example 500 errors and timeouts) Makes the difference beetween permanent and reflected XSS vulnerabilities. How to get the best results =========================== To find more vulnerabilities (as some attacks are error-based), you can modify your webserver configurations. For example, you can set the following values in your PHP configuration : safe_mode = Off display_errors = On (recommended) magic_quotes_gpc = Off allow_url_fopen = On mysql.trace_mode = On Where to get help ================= In the prompt, just type the following command to get the basic usage : python wapiti.py -h You can also take a look at the manpage. If you find a bug, fill a ticket on the bugtracker : https://sourceforge.net/p/wapiti/bugs/ What is included with Wapiti ============================ Wapiti comes with : + a modified version of PyNarcissus (MPL 1.1 License), see https://code.google.com/p/pynarcissus/ + Kube CSS framework ( see http://imperavi.com/kube/ ) and jQuery for HTML report generation. Source code structure (wapitiCore directory) ===================================== . |-- attack # attack modules used for the vulnerabilities Wapiti can detect | |-- __init__.py | |-- attack.py # Base for all attack modules | |-- mod_backup.py # This module search backup of scripts on the server | |-- mod_blindsql.py # Time-based blind sql scanner | |-- mod_crlf.py # Search for CR/LF injection in HTTP headers | |-- mod_exec.py # Module used to detect command execution vulnerabilities | |-- mod_file.py # Search for include()/fread() and other file handling vulns | |-- mod_htaccess.py # Try to bypass weak htaccess configurations | |-- mod_nikto.py # Use a Nikto database to search for potentially dangerous files | |-- mod_permanentxss.py # Look for permanent XSS | |-- mod_sql.py # Standard error-based SQL injection scanner | `-- mod_xss.py # Module for XSS detection | |-- config | |-- attacks # Here are the text files where you can add payloads | | |-- backupPayloads.txt | | |-- blindSQLPayloads.txt | | |-- execPayloads.txt | | |-- fileHandlingPayloads.txt | | `-- xssPayloads.txt | | | |-- language # Compiled language files (.mo) | | |-- en | | | `-- LC_MESSAGES | | | `-- wapiti.mo | | |-- es | | | `-- LC_MESSAGES | | | `-- wapiti.mo | | |-- de | | | `-- LC_MESSAGES | | | `-- wapiti.mo | | |-- fr | | | `-- LC_MESSAGES | | | `-- wapiti.mo | | `-- ms | | `-- LC_MESSAGES | | `-- wapiti.mo | | | |-- reports | | `-- generators.xml # Database of report engines | | | `-- vulnerabilities # Info about vulnerability types (references etc) | |-- anomalies.xml | `-- vulnerabilities.xml | |-- file # XML parsers used by Wapiti | |-- __init__.py | |-- anomalyxmlparser.py | |-- auxtext.py | |-- reportgeneratorsxmlparser.py | `-- vulnerabilityxmlparser.py | |-- language # Manage internationalization | |-- __init__.py | |-- vulnerability.py # Common strings used by Wapiti | `-- language.py | |-- language_sources | |-- de.po | |-- en.po | |-- es.po | |-- file_list.txt | |-- fr.po | |-- generateSources.sh # Script to generate .po files from source code | |-- generateTranslations.sh # Script to compile .po files to .mo files | `-- ms.po | |-- net | |-- HTTP.py # Wrapper around python-requests, contains HTTP, | | # HTTPResource and HTTPResponse classes. | |-- __init__.py | |-- crawlerpersister.py # Class used to store and load scan status | |-- jsoncookie.py # Library to load and save cookies to JSON files | |-- jsparser | | |-- __init__.py | | |-- jsparser.py # Modified version of the PyNarcissus parser | | | | |-- lamejs.py # Home-made and lame JS interpreter using PyNarcissus | |-- lswww.py # HTML parsing is made here | `-- swf_parser.py # Home-made Flash SWF parser, not an ABC interpreter | |-- report # Report generators | |-- __init__.py | |-- htmlreportgenerator.py # The HTML generator is based on the JSON one | |-- jsonreportgenerator.py | |-- openvasreportgenerator.py # Needs some more work | |-- reportgenerator.py # Abstract class | |-- reportgeneratorinfo.py | |-- txtreportgenerator.py | |-- vulneranetxmlreportgenerator.py | `-- xmlreportgenerator.py | `-- report_template # Template used for HTML reports |-- css | |-- kube.css | |-- kube.min.css | `-- master.css |-- index.html |-- js | |-- jquery-1.9.1.min.js | |-- kube.buttons.js | `-- kube.tabs.js `-- logo_clear.png
Link :https://github.com/IFGHou/wapiti
WebPwn3r - Web Applications Security Scanner.
webpwn3r :- WebPwn3r - Web Applications Security Scanner.
How to use:
1- python scan.py
2- The tool will ask you if you want to scan URL or List of urls?
1- Enter number 1 to scan a URL
2- Enter number 2 to scan list of URL's
3- URL should be a full link with a parameters
same thing with the list of links.
WebPwn3r got below Features:
1- Scan a URL or List of URL’s
2- Detect and Exploit Remote Code Injection Vulnerabilities.
3- ~ ~ ~ Remote Command Execution Vulnerabilities.
4- ~ ~ ~ SQL Injection Vulnerabilities.
5- ~ ~ ~ Typical XSS Vulnerabilities.
6- Detect WebKnight WAF.
7- Improved Payloads to bypass Security Filters/WAF’s.
8- Finger-Print the backend Technologies.
|||
Sunday, June 11, 2017
RED HAWK - All In One Tool For Information Gathering, SQL Vulnerability Scanning and Crawling
RED HAWK - All In One Tool For
Information Gathering, SQL Vulnerability Scanning and Crawling
Features Of The Tool:
- Server detection
- Cloudflare detector
- robots scanner
- CMS Detector
- WordPress
- Joomla
- Drupal
- Magento
- Whois
- GEO-IP Scan
- NMAP Port Scan
- DNS Lookup
- SubNet Calculator
- Subdomain Finder
- Reverse IP Scanner
- CMS detection For Sites On the same server.
- Parameter Finder
- Error based SQLi Detector
- Crawler
- Basic Crawler {69}
- [ - ] Admin scanner
- [ - ] Backups Finder
- [ - ] Misc. Crawler
- Advance Crawler{420}
- [ - ] Admin scanner
- [ - ] Backups Finder
- [ - ] Misc. Crawler
Released Versions:
- Version 1.0.0 [11-06-2017]
Changelog:
- Version 1.0.0
- Initial Launch
Installation:
Run The Tool and
Type fix This will Install All Required Modules.
Usage:
- git clone https://github.com/Tuhinshubhra/RED_HAWK
- cd RED_HAWK
- php rhawk.php
- Use the "help" command to see the command
list or type in the domain name you want to scan (without Http:// OR
Https://).
- Select whether The Site Runs On HTTPS or not.
- Leave The Rest To The Scanner
Subscribe to:
Comments (Atom)